You haven't signed in yet, you can have a better experience after signing in
 iDefender Infinite Potential Host Intrusion Prevention System HIPS
iDefender Infinite Potential Host Intrusion Prevention System HIPS

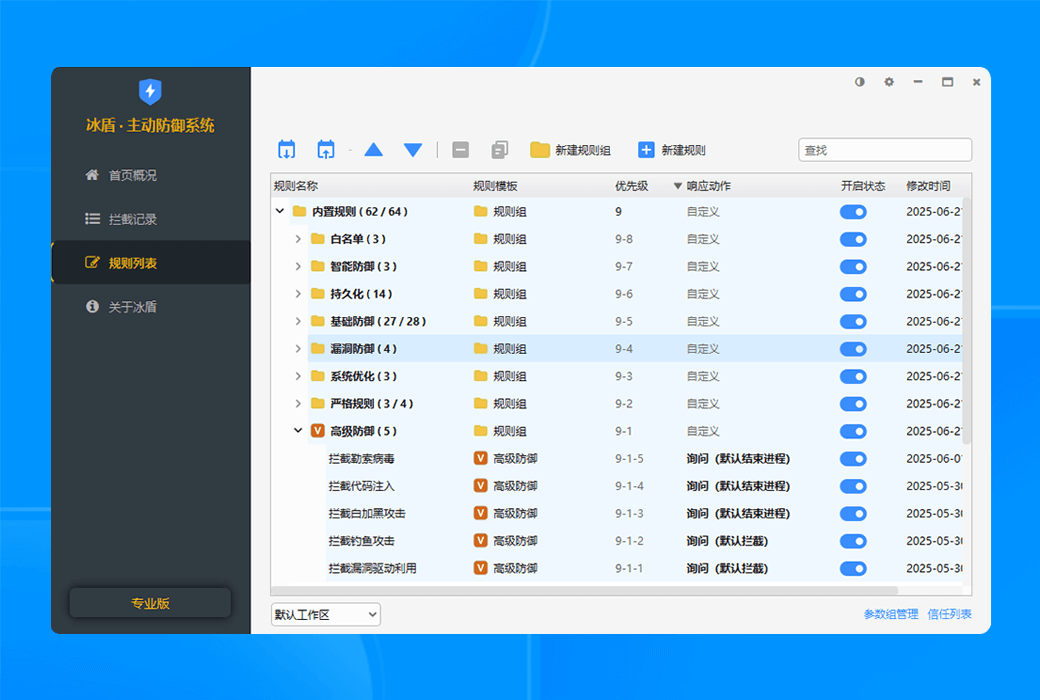
Activity Rules
1、Activity time:{{ info.groupon.start_at }} ~ {{ info.groupon.end_at }}。
1、Activity time:售完为止。
2、Validity period of the Group Buying:{{ info.groupon.expire_days * 24 }} hours。
3、Number of Group Buying:{{ info.groupon.need_count }}x。
Please Pay Attention
1、Teamwork process: Join/initiate a Group Buying and make a successful payment - Within the validity period, the number of team members meets the activity requirements - Group Buying succeeded!
2、If the number of participants cannot be met within the valid period, the group will fail, and the paid amount will be refunded in the original way.
3、The number of people required and the time of the event may vary among different products. Please pay attention to the rules of the event.
New Era of Terminal Security: A Revolutionary Breakthrough from Asynchronous EDR to Real time Protection
In the wave of digital transformation, terminal devices have become the most critical yet vulnerable link in the enterprise network security defense line. Traditional malware attacks are gradually evolving into more covert and complex forms of advanced threats, among which innovative attack techniques such as file free attacks and memory Shellcode injection are completely reshaping the landscape of terminal security protection. These new attack methods completely overturn the traditional security concept based on file feature detection, making traditional antivirus software (AV) that relies on static feature code detection inadequate in terms of protection effectiveness.
Terminal Detection and Response (EDR) technology has brought new hope to terminal security. The essential difference from traditional AV is that EDR adopts dynamic behavior analysis technology, which constructs a detection system capable of identifying abnormal behavior patterns through real-time monitoring of system process behavior, API call sequences, network communication patterns, and other deep system activities. This behavior analysis based protection concept can theoretically effectively respond to various unknown threats, including file free attacks and memory Shellcode.
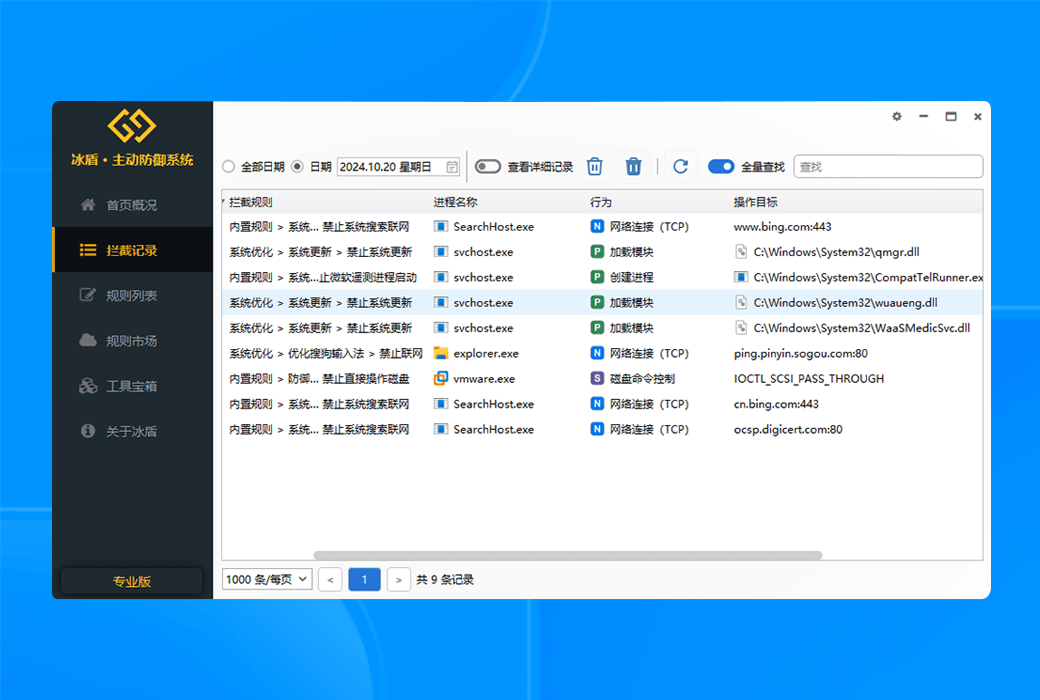
However, the current mainstream EDR solutions have a fatal architectural flaw - asynchronous detection mechanism. A typical EDR product adopts a "execute first, analyze later" working mode: the terminal only deploys lightweight data collection agents and uploads all behavior logs to the cloud analysis platform for post detection. This design leads to an unavoidable security paradox: by the time cloud analytics platforms finally discover a threat, the attack often has already completed its destructive operation.
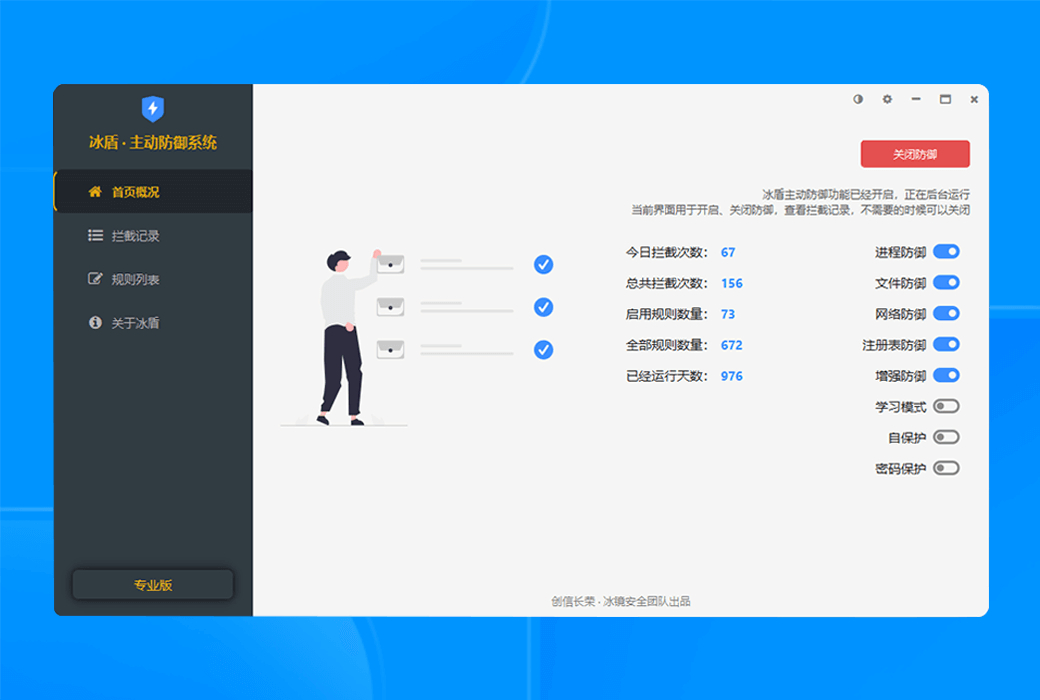
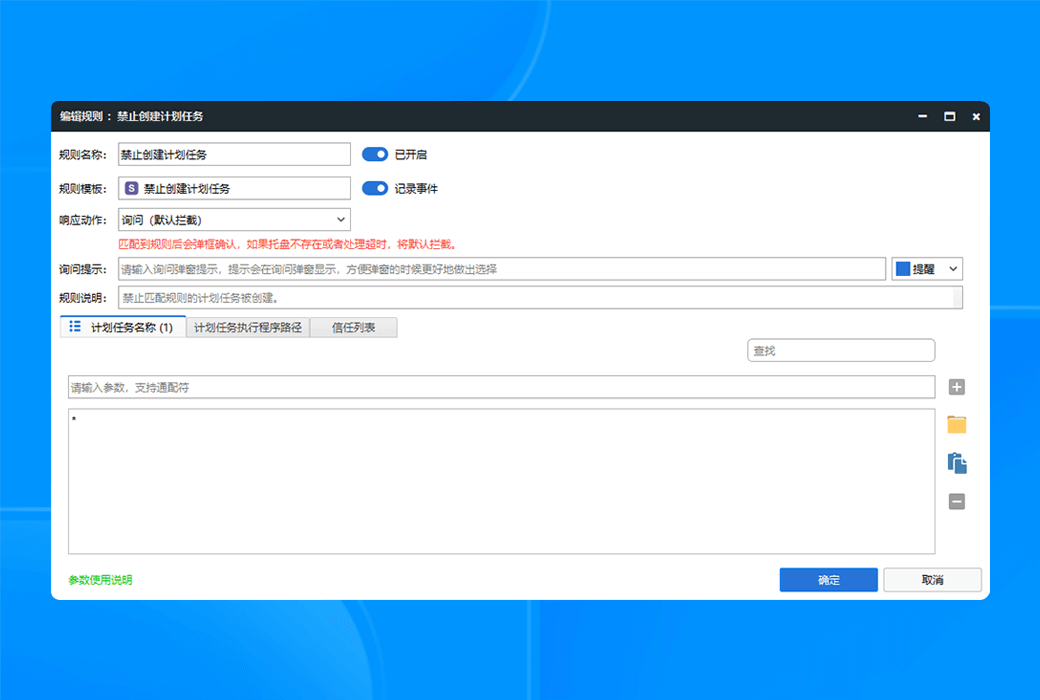
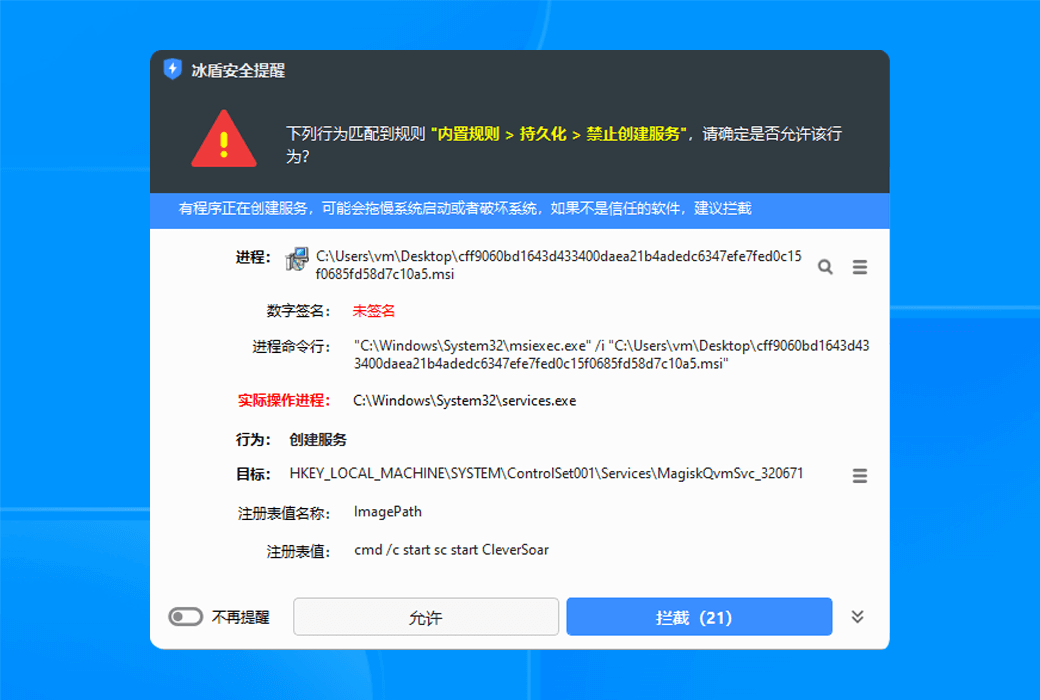
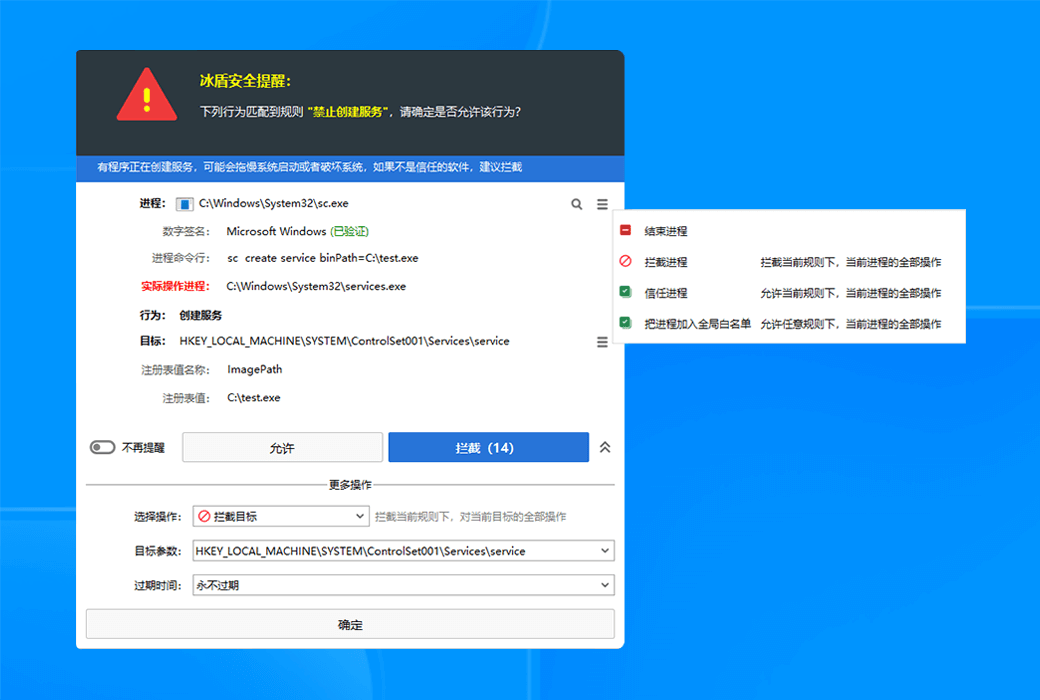
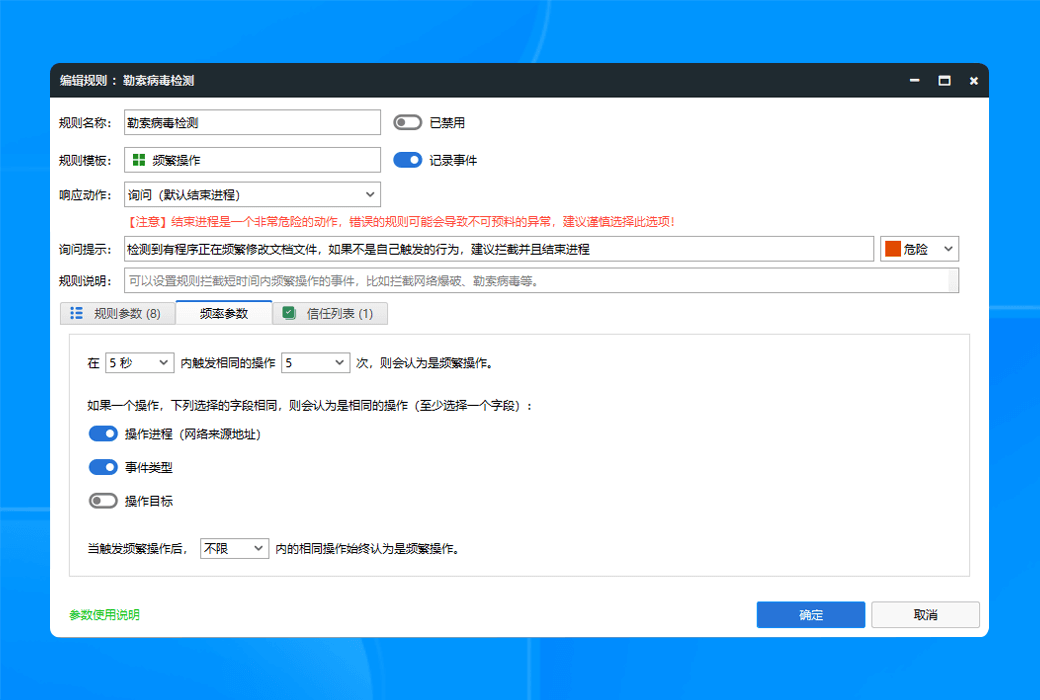
To completely solve the asynchronous detection dilemma of EDR, we have developed a groundbreaking new architecture for real-time terminal protection. This technology revolutionary brings advanced threat detection capabilities from the cloud directly to terminal devices, achieving a qualitative leap from "post detection" to "real-time interception" through localized real-time analysis engines. This innovation not only fills the protection gap of traditional EDR, but also redefines the timeliness standard of terminal security protection.
Usage scenario
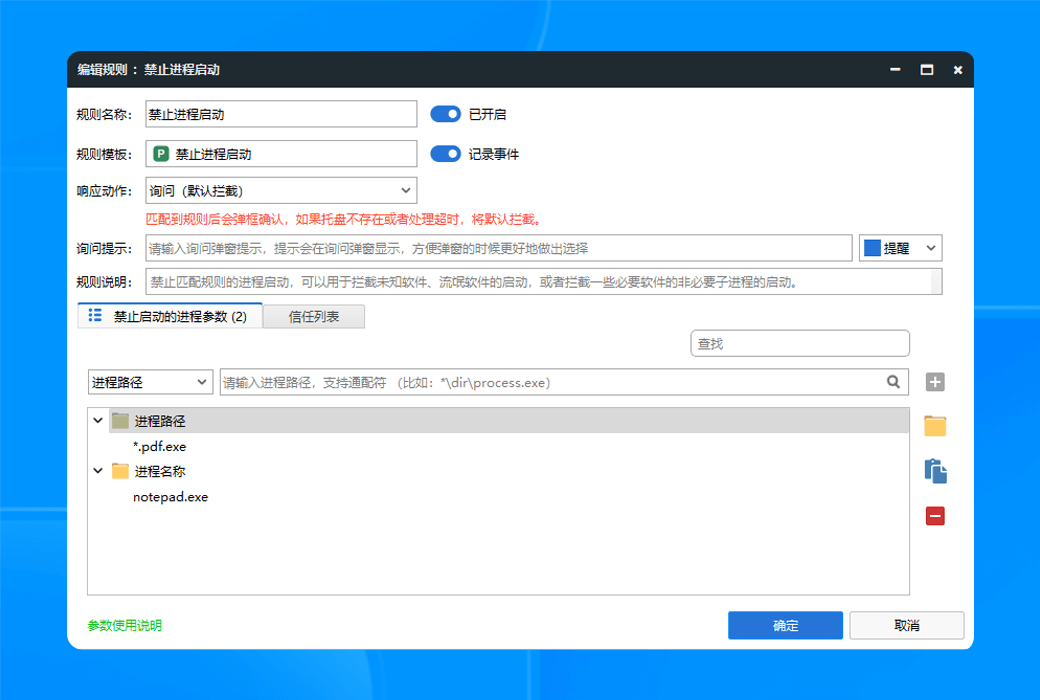
- Advanced threat protectionReal time interception of malicious behaviors such as file free attacks and memory Shellcode injection.
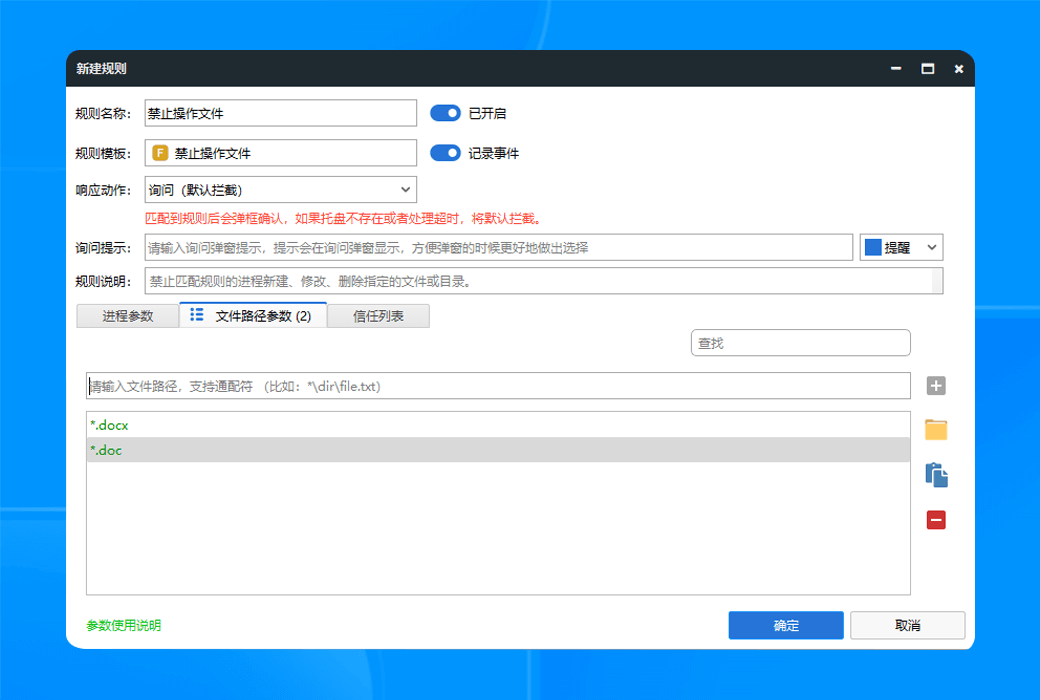
- Document ProtectionReal time monitoring of ransomware encryption process, precise detection and interception of ransomware.
- Process interceptionIntercept malicious behavior of rogue software and protect your computer system from being invaded by malicious software.
- Privacy ProtectionMonitor and prevent rogue software from stealing and uploading your personal privacy, protecting your data from illegal acquisition and abuse.
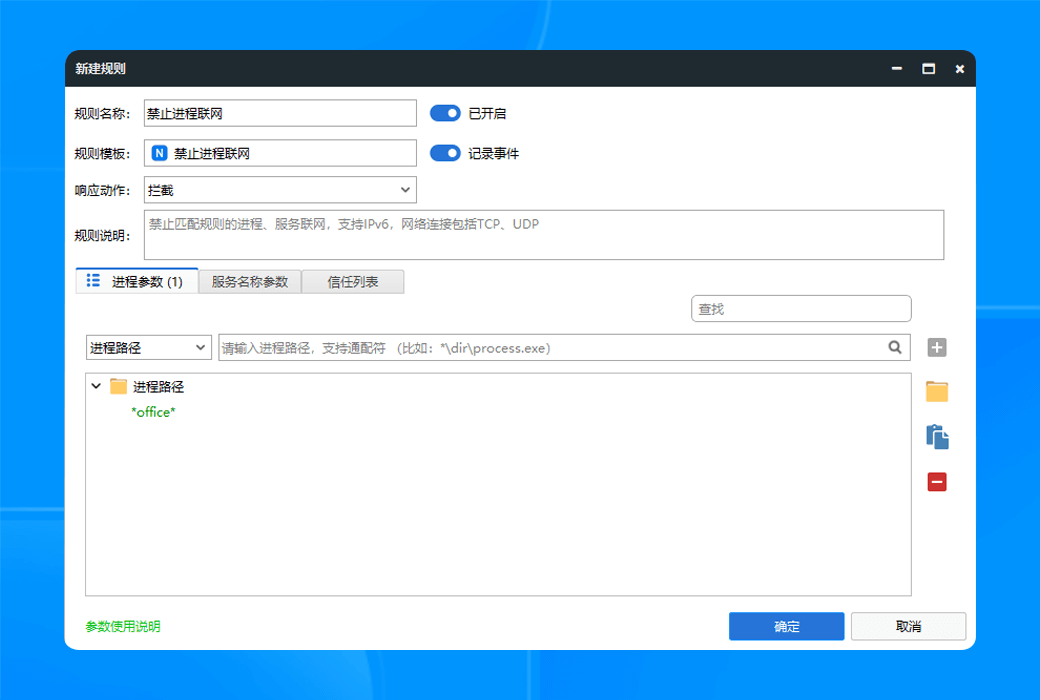
- Network controlMonitor network traffic, prevent personal information leakage and network attacks, and protect your personal privacy.
- Internet ManagementBy managing and controlling your online behavior, we ensure your network security and prevent the infringement of harmful information.
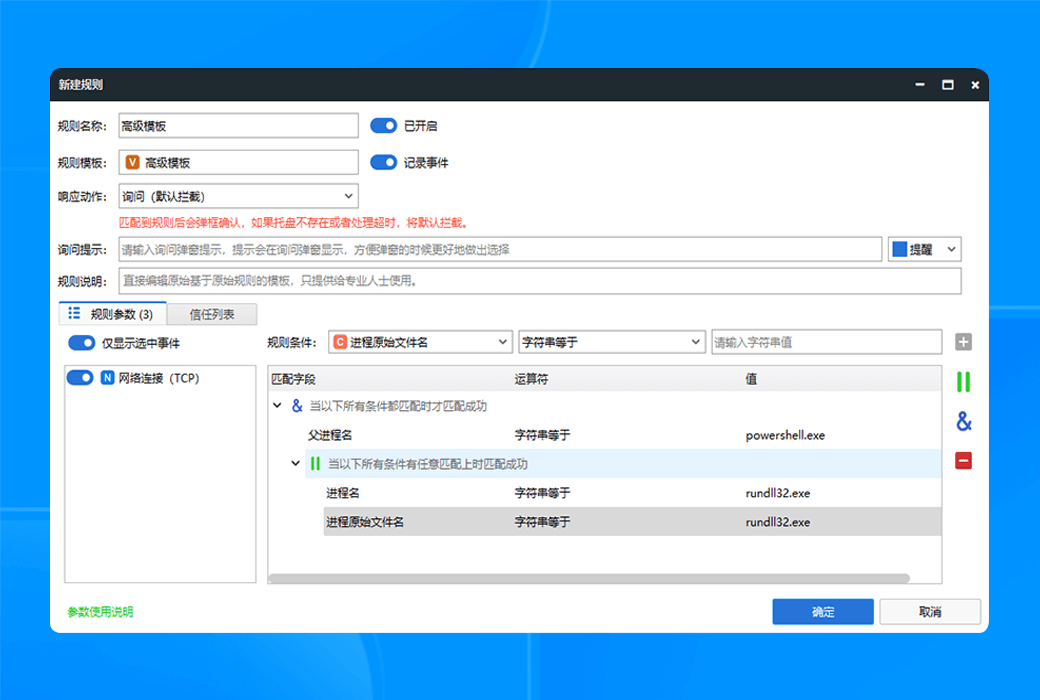
- Process GuardianPrevent malicious programs from injecting and terminating processes, protecting system stability and security.
- Safety sandboxFor unknown programs, they can be configured to run in a secure sandbox without damaging the system.
- Host SecurityProvide multi-layer security protection mechanisms to protect servers from hacker attacks and malicious software intrusion.
- Virus blocker Automatically intercept viruses through AI engines, providing real-time virus interception and removal functions.

Official website:https://trustsing.com/idefender/
Download Center:https://idefender.apsgo.cn
Backup Download:N/A
Delivery time:24-hour automatic shipping
Operating Platform:Windows
Interface language:Supports Chinese interface display and multiple language options.
Update Description:Use and update within the validity period, lifetime version supports permanent use, minor version updates, v5.x。
Trial before purchase:Free trial is available before purchase.
How to receive goods:After purchase, the activation information will be sent to the email address at the time of placing the order, and the corresponding product activation code can be viewed in the personal center, My Orders.
Number of devices:It depends on the version purchased.
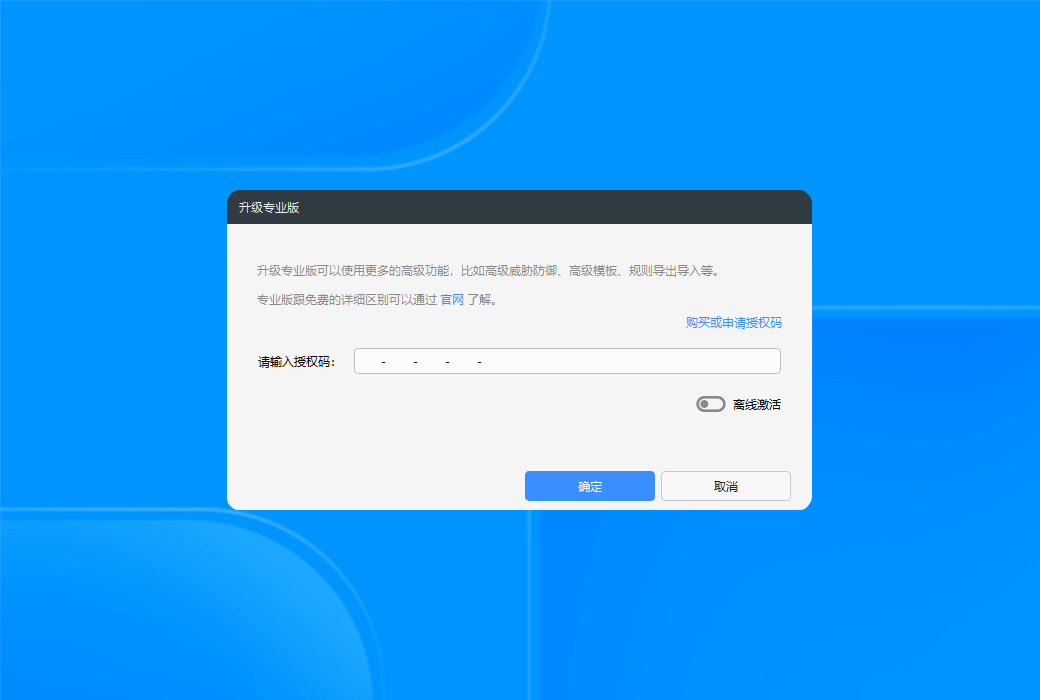
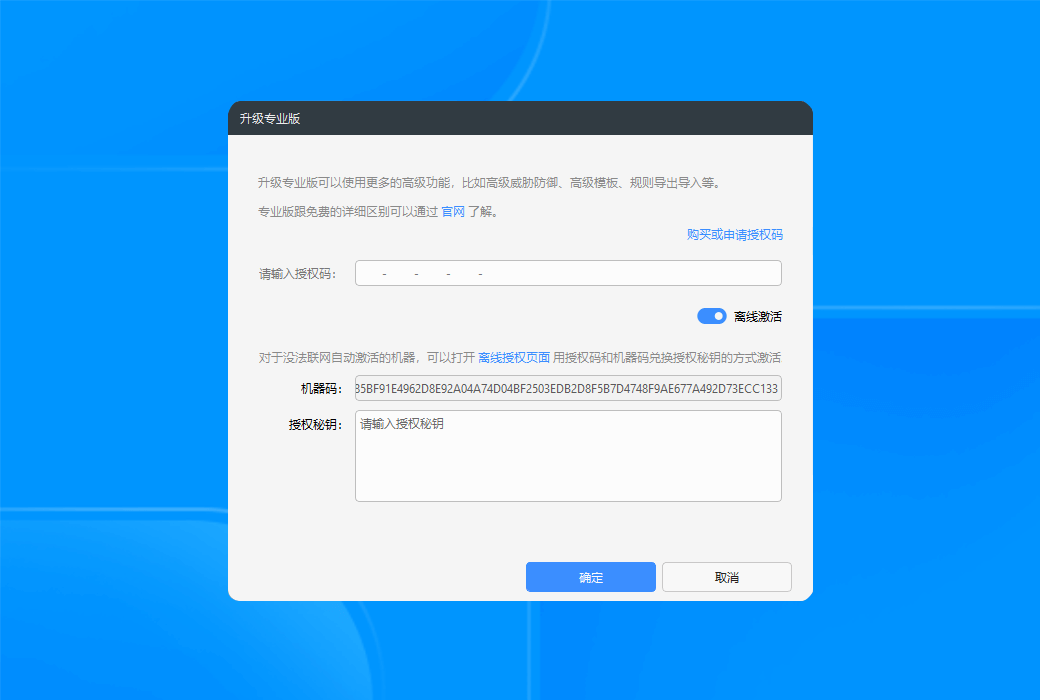
Replace computer:After activating the authorization, be sure to first save the authorization license number (in the professional version of the settings interface), and then use this link based on the authorization code and license numberRecycling authorizationCan be recycled online.
Activation guidance:To be added.
Special note:Authorization activation will bind the device. If you need to change the device or reinstall the system, please be sure to revoke the authorization before making the change, otherwise you cannot reactivate other devices.
reference material:https://trustsing.com/idefender/tutorial/ui.html

Any question
{{ app.qa.openQa.Q.title }}